Whether or not you believe data is really the new oil, there is no denying its value in today’s economy. Trillion-pound companies like Google/Alphabet make so much money because they trade their services for users’ data. And the processing of user information is central in the technology ecosystems of countless more billion-pound businesses.
However, the rush to innovate and deliver new products and services in a competitive technological landscape often results in data privacy being tacked on as an afterthought in the design of software, services, and products that process users' data. This leads to a situation where data privacy doesn’t seem to get prioritised anywhere near the same extent as collecting and using that data. High-profile data breaches continue to occur and affect people on massive scales.
-1.png?width=795&height=795&name=Linkedin%20post%20(1)-1.png)
Personal data sources continue to provide immense value for both good and bad reasons.
As individuals and regulatory bodies start to care more about data privacy, it’s no longer tenable to neglect privacy during design and development. Backing this up is recent guidance from the Information Commissioner’s Office (ICO) on privacy in the product design lifecycle. This article explains the idea of privacy by design and lists some compelling reasons why your organisation should move toward this approach.
What Exactly is Privacy by Design?
Privacy by design embeds and engineers data privacy best practices from the outset into the design and development of products, software, and services that process user data. This means deploying technical and organisational measures that place privacy at the heart of a product or service’s core functionality. Privacy by design also means putting in place countermeasures that anticipate and prevent data privacy breaches from the outset.
The idea of privacy by design actually stretches back quite far to the mid-1990s, when Ann Cavoukian pioneered the concept. Her basic stance was that complying with the rules outlined in regulatory frameworks alone doesn’t suffice to fully protect privacy. Rather, the best approach is for companies to aim to assure privacy by default in the design and architecture of products and services, independent of regulatory requirements.
What Does the ICO Say About Privacy By Design?
As alluded to in the opening, the ICO has also established guidelines on privacy by design aimed at product and UX designers, software engineers, QA testers, and product managers.
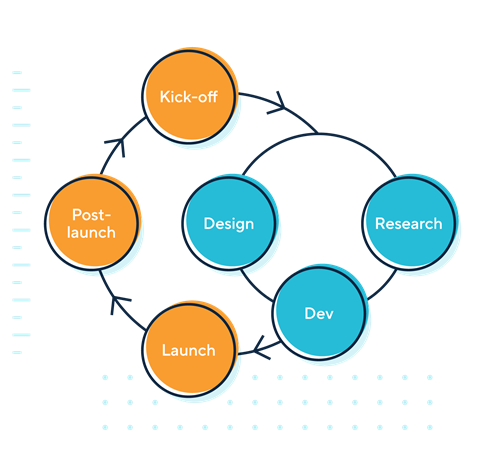
The ICO’s guidance includes a set of legislative “musts” alongside good practices (shoulds and coulds). Included in the set of factors to think about and implement are:
- How to weave data privacy into whatever business case a proposed product or service fulfils.
- How to effectively research the privacy expectations of the users you’re marketing your product or service to so that you’re less likely to violate what they want or expect.
- How to obtain valid consent to process data and communicate clearly how you’ll be using that data.
- Evaluating technical solutions and safeguards that protect privacy both during and after development.
- Conducting final checks before launching a product or service to make sure it effectively safeguards data privacy.
These factors correspond with various product design phases, including kick-off, research, design, development, launch, and post-launch. An example of a legislative must is that you must have a lawful reason for processing personal information. A should is to avoid using real user data when prototyping or working with mock user interfaces.
Privacy by Design Benefits
With so many factors to think about and a complete change of mindset in design and development necessary to implement the ICO guidance, what are the actual benefits of privacy by design?
Regulatory compliance
The most important reason to adopt privacy by design is that many regulations mandate this approach. Article 25 of UK GDPR, for example, stipulates that as a data processor, you put in place appropriate technical and organisational measures “both at the time of the determination of the means for processing and at the time of the processing itself…in order to meet the requirements of this Regulation and protect the rights of data subjects.” In the often ambiguous world of legal speak, this is another way of saying you must implement data privacy by design.
The EU’s version of GDPR has a similar requirement for privacy by design. There are also many non-mandatory regulations that companies comply with, whether to help land contracts or because it’s expected in their industries. Many of these non-mandatory frameworks also call for privacy by design to achieve full compliance (and certification)—an example is ISO 27701.
Enhance your reputation
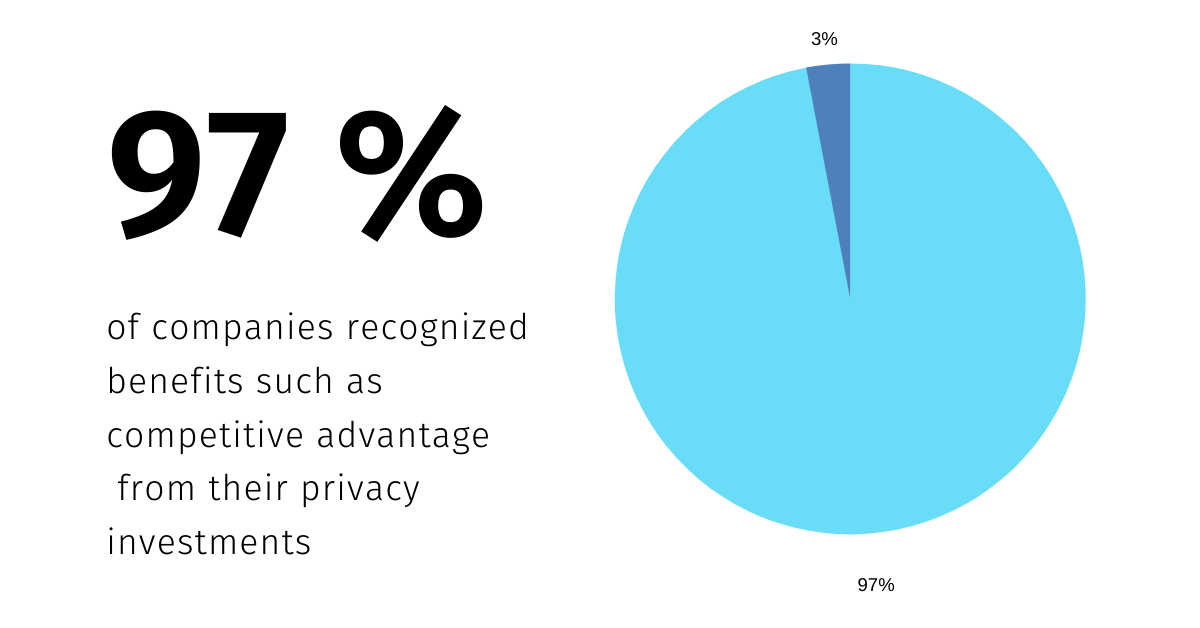
Source: CISCO CYBERSECURITY SERIES 2019 -Consumer Privacy Survey
Don’t downplay the reputational boost you get from demonstrating the central importance of data privacy in the design and core functionality of your products and services. In a digitally transformed world with more technological and privacy literacy, people and business partners truly value privacy.
In fact, a recent survey found 74 per cent of customers rank data privacy as a top value and concern. When you opt for privacy by design, you mirror your current and prospective customers’ core values and are far more likely to convince them to trust you to protect their data.
Reduce the cost of managing privacy risks
With the average cost of a data breach now exceeding £3.5 million, the cost/benefit analysis of privacy by design skews heavily in favour of moving to this approach. While some might make the argument that adding on privacy as an afterthought doesn’t guarantee a breach, today's threat actors are more sophisticated and technical than ever.
Knowing full well the value companies place in user data, this data is often the prime target of cyber attacks. And without privacy by design, any flaws or gaps in products or services that provide a path to data will almost certainly be found and exploited, leaving you with the cost and headache of a data breach. It’s almost certainly more cost-effective to manage privacy risks by baking protection in as a key aspect of design and development.
Protect individuals
Aside from the business-centric benefits of cost, compliance, and reputation from privacy by design, it’s also important to understand the responsibility to protect individuals. Enormous volumes of sensitive data reside in and move around IT ecosystems, and taking a proactive approach to privacy ensures you minimise the likelihood of privacy compromises.
Breaches or leaks can cause a significant impact on people's mental health from stress and anxiety. Finances can also be impacted when cybercriminals use stolen information to commit fraud against victims.
The 7 Principles of Privacy by Design
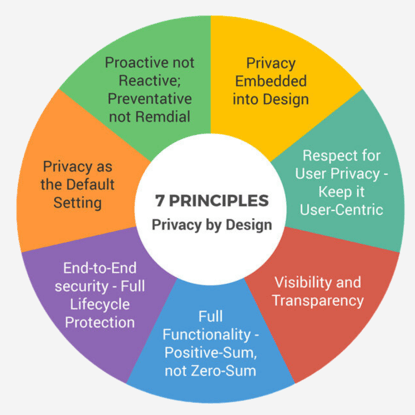
Here is a brief run-through of the seven foundational principles to understand if you want to implement privacy by design:
- Proactive not Reactive; Preventative not Remedial. You should be ready to predict, spot, and stop any privacy violations before they occur. This means you need to take action and implement countermeasures ahead of time, instead of after the fact.
- Privacy as the Default Setting. Don’t require users to take specific actions to ensure their data privacy is preserved. Instead, automatically protect privacy in systems and products that process data.
- Embed Privacy into Design. Make privacy integral to the design and architectural considerations of whatever system you’re designing rather than adding privacy-preserving features at a later point.
- Positive-Sum, not Zero-Sum. This means rejecting any trade-offs between privacy and other considerations, such as user experience or technical capabilities. The principle states that these considerations can all come together in a win-win scenario that doesn’t involve compromising any area.
- Full Lifecycle Protection. This principle calls for securely managing information across a system’s and the underlying information’s lifecycle, from before the first byte of information is processed until the data is safely discarded.
- Keep it Open. This principle requires transparency in terms of informing users about what data you’re collecting, what purpose it’s being used for, and how you plan to protect it.
- User-Centric. Following on from the previous principle, being user-centric means above all keeping the interests of the individual front and centre when it comes to privacy. This encompasses opt-ins, clear notices, consent, choices over disposal, and maintaining accurate information.
Get Outside Data Privacy Help
Among the many concerns companies face around processing and protecting information, moving to privacy by design can seem like a daunting task. Messy IT ecosystems and competitive landscapes that drive a focus on shiny new products, features, or services can see these initiatives fall by the wayside, even if they are desirable, guided by the ICO, and/or legally mandated.
That’s where tmc3 comes in with outside expertise that can accelerate your company’s move to privacy by design. Our range of consultancy services includes a variety of data protection services that help operationalise data protection and privacy, taking privacy by design from desirable to actionable.
%20(1).png?width=290&name=Team%20(5)%20(1).png)


COMMENTS