Taking a significant step towards strengthening national security, the Cabinet Office's Government Security Group, in collaboration with the National Cyber Security Centre (NCSC), has initiated a comprehensive review of cyber security postures across all government departments and selected arm's length bodies. This proactive initiative forms a crucial part of the advanced security regime, GovAssure, with the aim of protecting the IT infrastructure that supports vital public services from the growing wave of cyber threats.
Expanding on the foundation of the government's Cyber Security Strategy, GovAssure introduces rigorous annual security audits as a crucial step towards enhancing governmental resilience. In this article, we will explore GovAssure, providing insights into what government departments should anticipate and how they can prepare for assurance reviews.
Understanding GovAssure
GovAssure has been developed with the purpose of offering independent assurance that a system identified by a government department as crucial adheres to an adequate level of cybersecurity, as determined by the NCSC Cyber Assessment Framework (CAF).
GovAssure encompasses the CAF and incorporates an assurance component. The assessment involves the use of two tailored CAF profiles, which are similar to the existing process. However, GovAssure has now introduced five stages to the process. During stage 4, independent security assessments are conducted by specialist organisations such as tmc3. These assessments review the submission and evidence provided and evaluate whether the requirements are being met.
Understanding the CAF
The CAF was released originally back in 2018 as part of the Network and Information Systems Regulations (NIS). Originally, it was designed to be a measure of cyber resilience of Operators of Essential Services (OES) and Relevant Digital Service Providers (RDSP). In the subsequent years, many organisations adopted the CAF as their benchmark for cyber resilience, largely because it was created by the NCSC and widely regarded as best practice by the majority of public sector and a significant number of private sector entities. As a result of its widespread adoption, industry-specific profiles were later developed to cater to different sectors.
The CAF comprises 14 principles that are divided into 4 objectives. What sets it apart is its ability to go beyond simple pass/fail criteria. Instead, it allows for partial achievement and explicitly identifies areas that can lead to failure. This approach not only highlights what constitutes good cyber security practices but also calls attention to common pitfalls to avoid.
The below is an example of a contributing outcome.
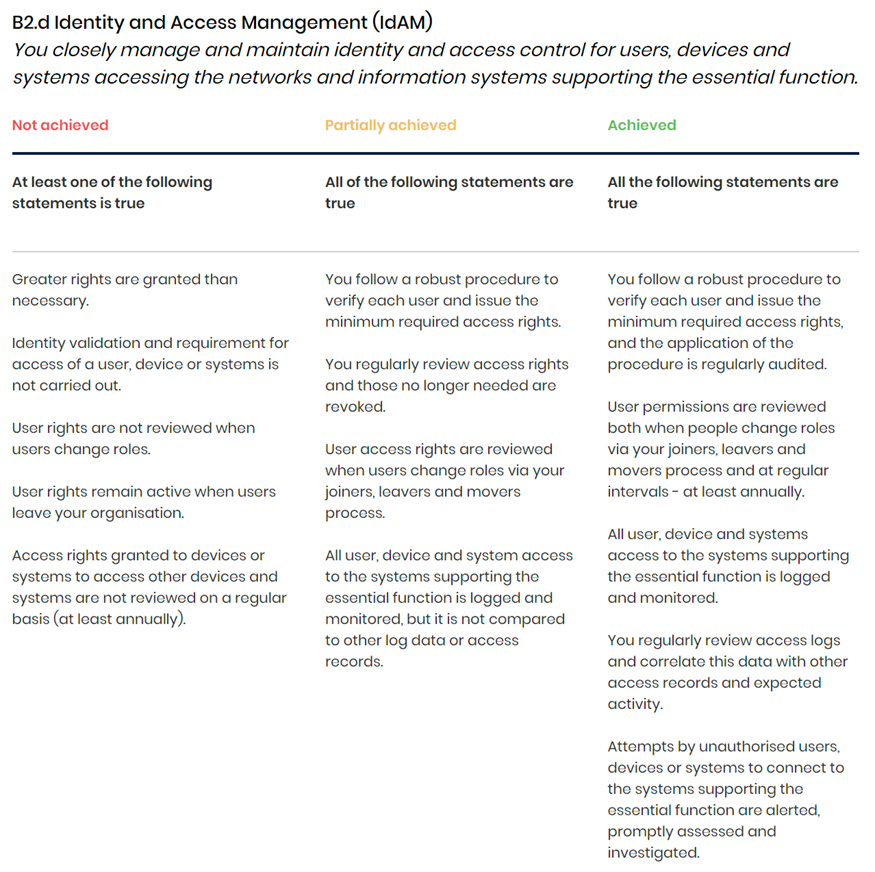
If any of the items in the "Not achieved" column are applicable, it results in the principle being classified as not achieved. It's worth noting that some items have contrasting outcomes between not achieved and achieved. For instance, granting greater rights than necessary is the opposite of issuing minimum required access rights. However, there are also some items that are not directly related to each other.
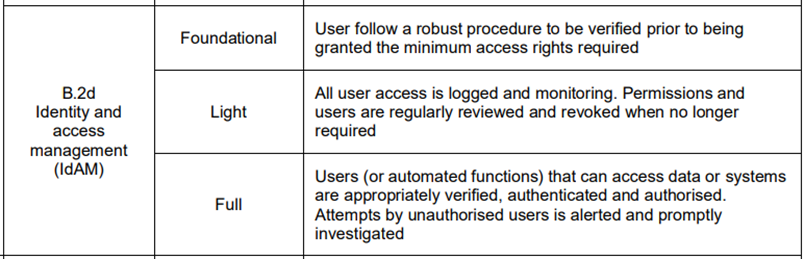
The level of partial achievement is when the profiles play a crucial role. For instance, when considering the energy sector's specific profiles, it corresponds to three distinct levels.
TOP TIP – You can view the requirements for both the GovAssure Baseline and Enhanced profiles on the Government Security website - https://www.security.gov.uk/guidance/govassure/government-caf-profiles - You need to login with a @gov.uk domain name to access this information.
How does the CAF become GovAssure and what is the process?
As mentioned above, the biggest shift is the requirement to gain independent assurance from a third party. In contrast to other schemes like IASME, the assurance bodies have greater flexibility in conducting the process. For instance, tmc3 will conduct interactive workshops to thoroughly review the responses, ensuring a complete and realistic understanding with proper context. This approach helps to enhance the overall effectiveness of the process.
In addition, the process for any remediation is defined, under Stage 5. The assurance body will generate a report, which will then be utilised by the organization and the Government Security team to develop a Targeted Improvement Plan, commonly referred to as a "Get Well Plan", outlining the necessary steps for improvement and resolution.
How can Government Departments prepare?
The UK Government security are still working on the final details and artefacts for GovAssure but the 5 steps have been published with a high level overview on their website. Stage 1 and 2 are collaborative efforts between the organisation and Government Security.
In Stage 1, the focus is on identifying and documenting crucial information about the organization's missions, objectives, and priorities. This process leads to the completion of the GovAssure Scoping Document Part A, which can be accessed through the provided link under stage 1 on the website mentioned above.
Moving on to the second part of stage 1, it involves identifying the essential services that fall within the scope. These services are categorised into three areas: Critical National Infrastructure, Operators of Essential Services (both of which are related to NIS), and Fundamental organisation outputs and missions. Examples of the latter include ministerial briefings and policy development. All this valuable information is then recorded in the same scoping document.
Continuing to Stage 2, the initial part involves identifying critical systems in Part C of the scoping documents that are necessary for operating the previously defined essential services. In Part D, these systems are recorded and prioritised, with a recommendation of submitting no more than 4 critical systems annually. It's important to note that Government Security will review this list before it is submitted for assessment.
The second part of Stage 2 entails working with Government Security to assign a profile, either Baseline or Enhanced, based on consultation and collaboration.
In Stage 3, organizations are responsible for conducting a self-assessment using the new WebCAF system created by Government Security. However, it is important to note that evidence must be shared through an existing organisational system as WebCAF does not currently handle this aspect due to the diverse requirements of GovAssure. The Stage 3 guidance provides a good level of detail around stakeholders who likely need to be involved for each section and also general guidance on the level of detail to provide. Government Security will also review the assessment before it moves onto stage 4.
TOP TIP – There is mapping between NCSC CAF and ISO27001:2013, ISA62443-3-3: 2013, ISA 62443-2-1: 2009, COBIT 5, CIS CSC and NIST SP 800-53 Rev.4 - https://www.security.gov.uk/guidance/govassure/stage-3
During Stage 4 of the process, the assurance body conducts a comprehensive review of the information. As mentioned earlier, this stage is not fixed and is typically led by the assurance provider. However, it is crucial for the organisation to feel comfortable with the process during the procurement stage of selecting an assurance provider. As an example, tmc3, facilitates workshops that cover Sections A and D separately from Sections B and C. This approach is tailored to accommodate different audiences. Alternatively, some assurance providers may choose to conduct the review offline.
Stage 5 is where the organisation receives the comprehensive report from the assurance provider. Working hand in hand with Government Security, the organisation will then craft a dynamic Targeted Improvement Plan, commonly referred to as the "Get Well Plan". This plan takes into account any existing or planned security projects, ensuring a holistic approach to enhancing cyber security resilience.
tmc3 - A cyber security partner for the digital era
Navigating the cyber security challenges in the public sector is easier when you have a cyber security partner. tmc3’ has vast experience helping organisations implement the CAF requirements and be ready foo GovAssure assurance checks. tmc3 is also an approved provider of GovAssure Assurance through the CCS Cyber Security Services 3 DPS (RM3764.3).
%20(1)-1.png?width=290&name=Team%20(3)%20(1)-1.png)


COMMENTS