Haven’t we already said this before?
No, you are not imagining it, this month (10 January 2023) marks the end of ESU or Extended Security Updates thus signalling the end of the line for Windows 7. ESU was an option Microsoft offers commercial customers to pay a significant sum of money to keep receiving critical security updates, allowing for Windows 7 to be used after ending free security updates on 14 January 2020.
Windows 7 was released back in late 2009 and it was an important release for Microsoft, both commercially, after widespread complaints about its predecessor, Windows Vista, and even more importantly technologically. At the time, Windows XP was fast approaching the originally planned end of extended support date. This meant that Windows 7 became the only real option for commercial customers.
Secondly, if we rewind back to the era that Windows 7 thrived in, it was the last Windows release before consumption changed to what we now see as the norm. Since 2020, more web traffic has come from mobiles browsers than desktop computers, apps are the new normal and consumption is often browser based.
A very different worldContrast this to when Windows 7 was released. Thick client apps written in Java and the like led the pack, these often had client pre-requisites such as Java Runtime. By the time Windows 10 was released in 2015 web apps were the default option. With that in mind many of the applications that were developed for the Windows 7 era were simply not being updated to run on newer underlying technology. Don’t get me wrong, it was a lot smoother of a ride that the XP - 7 path - those that are old enough to remember will no doubt still have nightmares about this transition.
However, even in 2020 and today in 2023, there is still a large number of systems that only work on Windows 7. This presumably is one of the big reasons that according to statcounter, even in December 2022, 11.2% of devices they sampled were still Windows 7. The actual number is likely to be higher due to most organisations having locked down Windows 7 devices to not allow internet access.
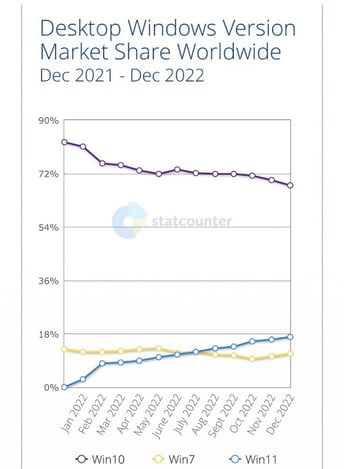
Statistics of Windows Versions in use as at December 2022
What should I do if I have old devices?
The most important question is for organisations who still have Windows 7 - what should you be doing and how concerning is it?
Of course the ideal scenario is to upgrade, it is often misunderstood why devices cannot be upgraded, as mentioned above the upgrade path is not as significant as previous major updates. Understand exactly why the device is still in service, it will likely be a specific service, for example it is unlikely that a web application will not run on Windows 10/11.
However, you should reach out to the vendor of the application that cannot run on newer operating systems. Many will have workarounds, especially if you operate in a regulated or risk aware industry such as finance or healthcare.
What if I cannot upgrade?
There is a chance you may still not have a sensible upgrade route, for example excessive upgrade costs. Fundamentally you then need to understand how bad it is to stay on an unsupported system; the answer to this is “it depends”. As per industry best practice including NCSC (Obsolete products - NCSC.GOV.UK) there are 2 important things to do to help reduce the risk, this comes back to the regularly used likelihood and impact methodology.
So, how do you reduce the likelihood of being compromised? To understand this we first need to understand how attacks happen. It is still the case that the majority of compromise is initiated via user interaction. This may be end user clicking on phishing emails and browsing malicious/ compromised websites or an IT user due to misconfiguration for example exposing services such as a web server to a wider network such as Wide Area Network (WAN) or even the internet.
Here are 4 ways to reduce the likelihood of compromise:
- Only use the device for what it is needed for. If possible, enforce this with network rules, for example only allowing the device to access the server for the required application, use a secondary supported (such as Windows 10/11) device for day to day actions.
- Do not use the device for web browsing (Google Chrome is also no longer supported on Windows 7) or to view email, these 2 things are the most common exploit. Also avoid plugging untrusted removable media into the device.
- Validate the posture of the device by looking outside in. Running a basic network scan using a tool such as NMAP from another device on your network will allow you to see what exposure the device has. Every exposed port is another service that is ever more likely to have a vulnerability and use firewalls (either network or the built in windows one) to restrict these services to only endpoints that need to access it.
- Consider the use of specialist tools. Often called virtual patching, available from various vendors for example the Trend Micro Apex One product offers virtual patching for Endpoints. These are specialist Intrusion Prevention Systems installed on hosts looking for network traffic that is attempting to exploit a vulnerability. This is not a silver bullet but they can be a good layer for defence in depth.
Looking at impact, it comes down to good business continuity and disaster recovery plans. Often legacy systems are harder to rebuild - trying to find that Windows 7 bootable USB buried in the drawer springs to mind.
However, as with all planning, assume full compromise is possible and plan accordingly. Only run what is absolutely necessary (as also covered above) and try and remove single points of failure. Be aware that legacy systems are often on older hardware that has a limited lifespan.
Ultimately no computer or system is ever 100% secure, however it can only be compromised in a limited number of ways, reduce those mechanisms and risk can be managed while you attempt to ultimately migrate.
Hang on, what about Windows Server 2008/ R2
The patient people who have got to the end of this article are probably wondering “what about Windows Server 2008/ R2” - the simple answer is that could be a whole other article. However, to summarise, a lot of the same things apply, the main difference is servers are generally easier to lock down to specific systems as they should generally be single user in the first place. In addition, intrusion prevention systems such as Trend Micro Cloud One Workload Security have additional signatures/rules to cover server functions such as Web Servers. As far as validation goes I always recommend prioritising a vulnerability and network discovery program to make sure you truly understand what you have on your network.
And finally for the very patient, Windows 8 and 8.1 also go end of life this month but its fair to say that at 2.6% usage (based on statcounter) its much less of an issue but the same advice applies.
Should you need any further guidance or would like to talk to us today about your security needs, please Get in touch with our expert team, today.
%20(1)-1.png?width=290&name=Team%20(3)%20(1)-1.png)


COMMENTS